Class Video – Mikrotik VPN
This class covers:
The slides are here: Mikrotik-VPN-Class (54931 downloads)
The video is around 1 hour and 15 minutes long.
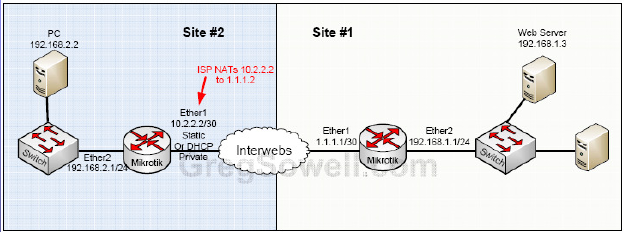
Here is my sophisticated lab:
A quick note on the video, I recorded it at 2 in the morning…sometimes it’s hard for me to find time. If you run into a little quiet space in the video, just chalk it up to being so late…hehehe.
And here is the video:
Using the packet flow diagram from the wiki, you can see that the src-nat operation will be performed before the packet gets encapsulated. This is why you have to do the src-nat accept for traffic that should traverse the tunnel.
One VPN topic I didn’t cover is PKI or certificate based VPN. This allows you to use a certificate instead of using a shared key for phase 1 negotiation. This one will be quite time consuming video wise, so I’m creating a separate video just for him.
I’ve got an article on IPSec or other tunneling protocols when BOTH sides have DHCP here.
If a single side has DHCP, then try this:
Site #1 will have peer address of 0.0.0.0 with “Generate Policy” checked. No policy is necessary (this is the same as is shown in the video and slides).
Site #2 will be configured the same as in the video, only you need to add this script:
1 2 3 4 5 6 7 8 9 | :local WANip [/ip address get [find interface="ether5"] address] :log info "Interface IP is $WANip" :local WANip [:pick "$WANip" 0 ([:len $WANip] - 3)] :log info "IP sans the slash notation is $WANip" /ip ipsec policy set 0 sa-src-address=$WANip |
Same script in command line form:
1 2 3 4 5 6 7 8 9 10 11 12 | /system script
add name=DHCP-VPN-UPDATE policy=\
ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive source=":local WANip\
\_[/ip address get [find interface=\"ether5\"] address]\r\
\n\r\
\n:log info \"Interface IP is \$WANip\"\r\
\n\r\
\n:local WANip [:pick \"\$WANip\" 0 ([:len \$WANip] - 3)]\r\
\n\r\
\n:log info \"IP sans the slash notation is \$WANip\"\r\
\n\r\
\n/ip ipsec policy set 0 sa-src-address=\$WANip" |
You will need to update the interface and the policy number to suit your needs. Schedule the script to run every 5 minutes or so.
This video covers L2TP for Windows client connections:
This video covers OpenVPN for remote offices connecting to a core:
Find the video HERE
As always, if you have any questions or comments, please leave them below. All I’m looking for is a little feedback. Also, if you enjoyed the video, consider visiting my sponsors and/or hit that donate button…I did invest a good chunk of hours building slides and recording/editing the video 😉





Umar,
If it powers down when you log in, you have big problems. It sounds like some sort of bug you have hit. If you aren’t running the most recent version of code, I would suggest upgrading. If you are, I would contact support to pursue the issue.
What version of ASA and MT are you using? We can’t get it to work at all with latest IOS and 5.0RC11
@Jefferson
ASA 8.X and MTK 3.30 and 4.X.
Here is the updated Cisco ASA 8.3+ version:
interface Ethernet0
nameif Outside
security-level 0
ip address 1.1.1.2 255.255.255.252
!
interface Ethernet1
nameif inside
security-level 100
ip address 192.168.2.1 255.255.255.0
!
access-list Outside_1_cryptomap permit ip 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0
!
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
!
object network LOCAL_HOSTS-192.168.2.0
subnet 192.168.2.0 255.255.255.0
object network REMOTE_HOSTS-192.168.1.0
subnet 192.168.1.0 255.255.255.0
nat (inside,outside) source static LOCAL_HOSTS-192.168.2.0 LOCAL_HOSTS-192.168.2.0 destination static REMOTE_HOSTS-192.168.1.0 RAVPN_HOSTS-192.168.1.0
object network ANY-0.0.0.0
subnet 0.0.0.0 0.0.0.0
nat (inside,outside) dynamic interface
!
crypto ikev1 policy 1
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
crypto ikev1 enable outside
!
route Outside 0.0.0.0 0.0.0.0 1.1.1.1 1
!
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map outside_map 1 match address Outside_1_cryptomap
crypto map outside_map 1 set peer 1.1.1.1
crypto map outside_map 1 set ikev1 transform-set ESP-3DES-MD5
crypto map outside_map interface outside
!
tunnel-group 1.1.1.1 type ipsec-l2l
tunnel-group 1.1.1.1 ipsec-attributes
ikev1 pre-shared-key test
!
*might also need:
sysopt connection permit-vpn
@Alex
Thank you sir!!!!!!!!!!
Hi Greg,
Great video. I’m struggling with a dynamic WAN IP endpoint setup. Say SiteA is static and SiteB is dynamic.
When i configure as you say in this video for a dynamic IP, the SiteA router gets the packet and i can see the debug result in the log however it fails and i get a ipsec debug message “couldn’t find configuration”
If i do a standard ipsec site to site with policies on either side and SiteB’s current WAN IP then the tunnel establishes fine. Any ideas?
Further to my post above, after cycling through a few different versions of rOS thinking it was broken – i tried the peer configuration noted like: 0.0.0.0/0 instead of just 0.0.0.0 and it established straight away! i wonder when that changed….
Excellent video. Thank you for taking the time to create it and share it! I’ve been working with Cisco equipment for years and have recently started diving into MikroTik. Your site is one of the most helpful sites I’ve come across yet.
And RJ, I ran into the same problem trying to set this up tonight and your comment got me going within about 5 seconds of finding it. So thanks for sharing the input as well!
Great video really cleared up the ip/ip ipsec I have been wanting to do
Hi Greg, thanks very much for your extremely useful and informative video. I work for a school and the consultants were going to charge us ‘an arm and a leg’ to set up VPN between our two sites. After using your videos to inform myself I was able to do the job myself in less than an hour. thanks again! Alan
@Alan
🙂 Always happy to help sir!