Video Guide to Configure OpenVPN in Mikrotik For Remote Offices
Use OpenVPN along with OSPF to have remote offices that dynamically create tunnels to a hub site and share routes dynamically between the two.
Create a self-signed certificate in Mikrotik:
1 2 3 4 5 6 7 8 9 10 11 | /certificate add name=ca-template common-name=myCa key-usage=key-cert-sign,crl-sign add name=server-template common-name=server add name=client1-template common-name=client1 add name=client2-template common-name=client2 /certificate sign ca-template ca-crl-host=192.168.88.153 name=myCa sign server-template ca=myCa name=server sign client1-template ca=myCa name=client1 sign client2-template ca=myCa name=client2 |
Questions/comments always welcome!


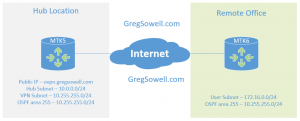
Thanks for the videos. We have Mikrotik Routers in a couple of data centers and our work network. I have been able to create several different types of tunnels. It is very useful to work remotely and gain access to devices on the work LAN.
However, I haven’t been able to figure out how I can forward all traffic across the tunnel. Preferably I would like to have a Mikrotik at home that all or some of the LAN Ports connect to my office Mikrotik, via a VPN, and gains access to internet through the office.
@Mike Look at some policy based routing either with “ip route rules” or creating a route in the route table with a routing mark, then mangle rules to change routing.