Class Video – Mikrotik VPN
This class covers:
The slides are here: Mikrotik-VPN-Class (55020 downloads)
The video is around 1 hour and 15 minutes long.
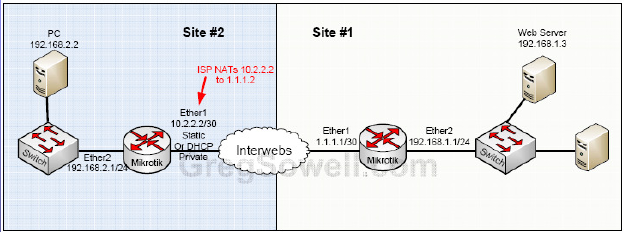
Here is my sophisticated lab:
A quick note on the video, I recorded it at 2 in the morning…sometimes it’s hard for me to find time. If you run into a little quiet space in the video, just chalk it up to being so late…hehehe.
And here is the video:
Using the packet flow diagram from the wiki, you can see that the src-nat operation will be performed before the packet gets encapsulated. This is why you have to do the src-nat accept for traffic that should traverse the tunnel.
One VPN topic I didn’t cover is PKI or certificate based VPN. This allows you to use a certificate instead of using a shared key for phase 1 negotiation. This one will be quite time consuming video wise, so I’m creating a separate video just for him.
I’ve got an article on IPSec or other tunneling protocols when BOTH sides have DHCP here.
If a single side has DHCP, then try this:
Site #1 will have peer address of 0.0.0.0 with “Generate Policy” checked. No policy is necessary (this is the same as is shown in the video and slides).
Site #2 will be configured the same as in the video, only you need to add this script:
1 2 3 4 5 6 7 8 9 | :local WANip [/ip address get [find interface="ether5"] address] :log info "Interface IP is $WANip" :local WANip [:pick "$WANip" 0 ([:len $WANip] - 3)] :log info "IP sans the slash notation is $WANip" /ip ipsec policy set 0 sa-src-address=$WANip |
Same script in command line form:
1 2 3 4 5 6 7 8 9 10 11 12 | /system script
add name=DHCP-VPN-UPDATE policy=\
ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive source=":local WANip\
\_[/ip address get [find interface=\"ether5\"] address]\r\
\n\r\
\n:log info \"Interface IP is \$WANip\"\r\
\n\r\
\n:local WANip [:pick \"\$WANip\" 0 ([:len \$WANip] - 3)]\r\
\n\r\
\n:log info \"IP sans the slash notation is \$WANip\"\r\
\n\r\
\n/ip ipsec policy set 0 sa-src-address=\$WANip" |
You will need to update the interface and the policy number to suit your needs. Schedule the script to run every 5 minutes or so.
This video covers L2TP for Windows client connections:
This video covers OpenVPN for remote offices connecting to a core:
Find the video HERE
As always, if you have any questions or comments, please leave them below. All I’m looking for is a little feedback. Also, if you enjoyed the video, consider visiting my sponsors and/or hit that donate button…I did invest a good chunk of hours building slides and recording/editing the video 😉





Thanks Greg, you are doing a very educative work. Been using Mikrotik for few years for bridge between work & home, and always wanted to do things like you explained here. Now you gave me a great kick forward to try this things, i want to connect a HQ and a few sites together via ADSL.. Wish me luck
Great Ivan,
Best of luck sir!
Would love to see the certificate based VPN tutorial. Its an area of information that really lacks when it comes to these devices and the only thing stopping me from purchasing 50 or so RB450G’s !!
I’ll look into knocking out a video on it soon…;)
BTW, unless you need to hold the full internet route table, I wouldn’t use a 450, I would use a 750G. Cheaper and better performance!
OK cool !! So you reccomend the 750G over the 450 ‘G’ model ? Even with the RAM difference. I am still having huge difficulties trying to find examples of MikroTik to MikroTik VPN’s – either OpenVPN or IPsec.
I have downloaded to software and have two routers set up in VirtualBox but cant seem to make any headway. I need a solution that will work with dynamic internet IP addresses via dynamic DNS. I know there are a few people who have had issues with IPsec VPN’s and dynamic IP’s.
Oh – and I need a terminal based tutorial !! We are an OSX house and will only be configuring via SSH / command line. No Windows GUI in this house !!!
You can run winbox via darwine…I know a guy that does it all the time 🙂
If you use Snow Leopard, try run winbox with WineBottler:
http://winebottler.kronenberg.org/
Darwine in SL doesn’t works very well…
J.
Thanks for the tip Javino!
wow! great work, thanks alot, do you have some mikrotik visual tutorials about bandwidth management like you offer before 🙂
Afridi,
It’s in the foreseeable future 😉
Thank you for the great work
Thank you, great videos!! Keep them coming 🙂
Alex,
Thanks, I’ll try to. I’m trying to wrap up my routing video…hopefully within the next couple of weeks!
Awsome explanations. I haven’t watched the movie, but i took a look at the ppt. On the ipip between mikrotiks i don’t understand 1 thing: you set everything to 1.1.1.1 and 1.1.1.2 or something like that, but you route all through 172.16.0.2. I think there should be 1 more step added where you add and ip address on the ipip interface (172.16.0.1 and 172.16.0.2 on the other end). Or am i wrong? only worked for me like that and also had to make a no nat rule when going from 1 lan to the other.
Radu,
You are correct sir. The PPT were really just notes to accompany the video. In the video you see me actually add the IP addresses to the interfaces. That was a great catch sir.
I have 1 more problem with IPSec iptunnel mode with mikrotiks. There was a power break at one of the locations. After the power came back the tunnel was down and i had to delete the IPSec config and recreate it. Any sugestions on how i could avoid this?
Setup DPD (dead peer detection). 15 seconds and 2 attempts is usually adequate. If a peer is down for this amount of time, it will clear out their SAs associated with that peer. You configure this under ip->ipsec->peer.
Thank That worked like a charm 🙂
🙂 Great Radu.
Hey Greg, I have a question about the NAT you built during the first IPSec setup. Wouldn’t it be easier to use the wonderful NOT (!) rule instead of creating 2 or more rules? ie –
/ip firewall nat add chain=srcnat dst-address=!192.168.0.0
/16 action=masquerade
There are many ways to skin a cat sir. I often create an access list and name it rfc1918 and just put all private addressing in there. I then create the nat bypass using the address list. 🙂
touché my friend, touché, LOL
Hehehehe 😛
nice tuts 🙂
i’ll try know 🙂
Hello.
I am very pleased with video materials on this site. it’s real life situations very well explained.
I am searching for solution where Mikrotik will act as cisco vpn client that will make connection with pix/asa when interesting traffic is matched. Pix/asa will ask for group user/password and there in Xauth also.
Could miktorik support thih scenario?
Thank you
Tik,
I don’t believe that the MTK can act as a xauth client. You can do standard IPSec tunnels, but I don’t believe the MTK will support the proprietary Cisco extensions.
Ok I suspected that but I want to ask.
I have vpnc on ubuntu and it works well as cisco vpn client for remote access but I will rather have vpn connection on router/MTK than on PC.
Anyhow
thank you and
good luck
Greg,
I’ve managed to create a working IPSec VPN between a Cisco ASA5505 and MikroTik 450/750 but after a few minutes it goes dead. I have to flush the installed SAs and then ping the remote network while in WinBox using the Bridge/ether2 interface to create interesting traffic, or I can ping the remote ASA network from a host behind the MikroTik – but it does not work the other way around. I.e. if I flush the installed SAs and then ping the MikroTik LAN from the ASA LAN it never creates interesting traffic.
The IPSec logs aren’t providing any information.
Have you seen this before between Cisco ASA and MikroTik?
Kevin,
I’ve seen similar, just not that quick. Try enabling dead peer detection on your MTK. It is on by default on your ASA.
Hey Greg, Followed your ppt to establish a site-to-site IPSec VPN from a Cisco ASA 55240 (site #2) to a MikroTik RB-450 (site #1). Slides 31 to 40. Am able to ping, ssh etc from Site# 2 to Site #1. But never from Site#1 to Site#2!! When I traceroute from site#1 to an internal IP in site#2, the packets appear to get stuck at the gateway at site#1 and doesn’t know where to go from there. Should I build a route even when its not a IPIP tunnel? Please help. Thanks much in advance.
Binay,
You won’t need a specific route if you have a default route on your device that will carry the traffic the proper direction.
When you attempt a connection from the ASA you are going from a higher security level to a lower, so the connection is allowed. When the MTK side traffic tries to establish connection to the ASA side it fails because it is coming from a lower to higher without the presence of a specific allowance. You can add an acl entry allowing it in the ASA or you can set that tunnel to “bypass interface acls” or the like; I can’t remember the exact nomenclature.
Thanks a lot, Greg.
On the ASA, I do have acl entries to let the traffic from MTK. But the thing is, when a ping is initiated from MTK side, it does not seem to even go beyond the MTK router. It’s not seem to be hitting the ASA at all or I would have seen a deny/drop message. Am checking if something’s wrong with the default route as you have mentioned in your first line. Any other clues to debug this, while am looking at the route?
When you use the ping tool, are you specifying the inside interface? You should be choosing the interface that has the private addressing that is to traverse the tunnel. You could alternately use a PC that is on this private subnet.
Hi Greg!
It finally worked after playing a bit around the firewall rules. Thanks so much for your tutorial. I also had to configure for supporting multiple subnets. I would never have guessed that choosing the “unique” option instead of “require” would do the trick, if not for your tutorial.
The connection appears to close itself after a brief period of inactivity, and I have to manually flush the SAs at the MTK side to make it work again. I did set up the DPD as per your tutorial. Am now trying to find out the exact period of inactivity that makes it drop the connection. Once again, thanks for sharing the tips.
Binay, that’s great!
Hi Greg, I have two RB450’s both behind Comcast Business Gateway’s. This is different than I have ever setup because the RB450’s are not acting as the primary router. What settings will be different as a result of two routers on each end? I can get an IPSec tunnel established, however I can only ping one direction to the other RB450 and I cannot ping any local hosts on either network. I am happy to share additional details about my config as needed.
Thanks in advance for any assistance you can offer.
Hi greg,
I started picking away at getting a mikrotik routerboard on dynamic IP behind NAT connected to a zyxel zywall 5 using IPSEC over 6 months ago and finally got it working, thanks to your slides & video.
I was about to give up!!!
thanks a lot
Craig,
Way to keep at it sir. You can’t let the machines win…then they will attempt their revolt!
Give me the subnets you are using.
Did you do your src nat accepts properly?
Do you have static IPs, or are they dynamic?
Hi Greg,
I have a question about l2tp over ipsec VPN client connection towards a Mikrotik RB450G. I am trying to connect a roadwarrior laptop (Mac) to the router configured as a l2tp server. Although the IPSec connection looks ok in racoon (on the mac side), pppd daemon(also on the mac) reports “L2TP cannot connect to the server”. On the mikrotik side, I’ve opened up in the firewall all the UDP ports. In the NAT section, I masq the LAN traffic towards Internet and L2TP server is active. PPP secrets is configured similar to your video setup and I still have not managed to open up the VPN. In the log, I do not see anything related to L2TP server.
Do you have any recommendations of things to check for this kind of setup?
Thank you,
Robert
19:31:04 ipsec respond new phase 1 negotiation: [500][887]
19:31:04 ipsec begin Identity Protection mode.
19:31:04 ipsec received Vendor ID: RFC 3947
19:31:04 ipsec received Vendor ID: draft-ietf-ipsec-nat-t-ike-08
19:31:04 ipsec received Vendor ID: draft-ietf-ipsec-nat-t-ike-07
19:31:04 ipsec received Vendor ID: draft-ietf-ipsec-nat-t-ike-06
19:31:04 ipsec received Vendor ID: draft-ietf-ipsec-nat-t-ike-05
19:31:04 ipsec received Vendor ID: draft-ietf-ipsec-nat-t-ike-04
19:31:04 ipsec received Vendor ID: draft-ietf-ipsec-nat-t-ike-03
19:31:04 ipsec received Vendor ID: draft-ietf-ipsec-nat-t-ike-02
19:31:04 ipsec received Vendor ID: draft-ietf-ipsec-nat-t-ike-02
19:31:04 ipsec received Vendor ID: DPD
19:31:04 ipsec Selected NAT-T version: RFC 3947
19:31:04 ipsec Hashing [500] with algo #2
19:31:04 ipsec NAT-D payload #0 verified
19:31:04 ipsec Hashing [887] with algo #2
19:31:04 ipsec NAT-D payload #1 doesn’t match
19:31:04 ipsec NAT detected: PEER
19:31:04 ipsec Hashing [887] with algo #2
19:31:04 ipsec Hashing [500] with algo #2
19:31:04 ipsec Adding remote and local NAT-D payloads.
19:31:05 ipsec NAT-T: ports changed to: [43929][4500]
19:31:05 ipsec KA list add: [4500]->[43929]
19:31:05 ipsec ISAKMP-SA established [4500]-[43929] spi:8fb62c4279d41066:a8f93d192376f10b
19:31:06 ipsec respond new phase 2 negotiation: [4500][43929]
19:31:06 ipsec Update the generated policy : 172.10.20.2/32[59269] /32[1701] proto=udp dir=in
19:31:06 ipsec Adjusting my encmode UDP-Transport->Transport
19:31:06 ipsec Adjusting peer’s encmode UDP-Transport(4)->Transport(2)
19:31:06 ipsec IPsec-SA established: ESP/Transport [43929]->[4500] spi=55443183(0x34dfeef)
19:31:06 ipsec IPsec-SA established: ESP/Transport [4500]->[43929] spi=153704848(0x9295990)
19:31:07 firewall,info input: in:ToInternet out:(none), src-mac 00:0a:8a:b0:59:80, proto UDP, :59269->:1701, len 68
19:31:26 ipsec generated policy, deleting it.
19:31:26 ipsec get a src address from ID payload 172.10.20.2[59269] prefixlen=32 ul_proto=17
19:31:26 ipsec get dst address from ID payload [1701] prefixlen=32 ul_proto=17
19:31:26 ipsec pfkey spddelete(inbound) sent.
19:31:26 ipsec purged IPsec-SA proto_id=ESP spi=153704848.
19:31:26 ipsec pfkey X_SPDDELETE failed: No such file or directory
19:31:26 ipsec pfkey X_SPDDELETE failed: No such file or directory
19:31:26 ipsec ISAKMP-SA expired [4500]-[43929] spi:8fb62c4279d41066:a8f93d192376f10b
19:31:27 ipsec ISAKMP-SA deleted [4500]-[43929] spi:8fb62c4279d41066:a8f93d192376f10b
Robert,
I’ve got no Mac experience, so I’m not sure where to steer you on that. Make sure tha tyou don’t have nat-t enabled on the MTK side…it seems to cause nothing but problems.
Did you ever manage to make l2tp + ipsec vpn server work in any of your works? I’ve read several posts on Mikrotik forum and it seems that others have similar problems even on the Windows side.
I never did get it working with Windows… unfortunately.
Thanks alot. I wait for another basic Mikrotik tutorial.
I am appreciative for the work you have done and how it has given me a great start with MikroTik. I have a tendency to over analyze and your videos keep me from doing that. Thanks!!!!
🙂
hey greg,
this is my first post and i am new to the networking scene… so forgive me if i misunderstand… i followed your PPTP instructions and when i try to remote desktop through the vpn my packet makes it though and is accepted but then the response back is dropped by my illegal destination address check… any idea why? i thought the tunnel was supposed to change the local ip back to my public ip.
Any light you could shine my way?
@Ed
Are you trying to RDP to something inside your private network, or to something on the internet? If you are traveling through the tunnel and then hairpinning back to the internet, be sure you have a src-nat masquerade rule that covers your PPTP IP address.
thank you for the explanetion Mr. Gregg. I have used you instruction to configure my router but when ever I tried to log on it power off so I have to diconnect and connect again to start it and after then it stand for hour untill I tried to connect again