So I am running CIQ Ascender which is built from the upstream Ansible AWX project(holler at me if you are looking for support), and to protect it as well as give it an SSL cert I use Cloudflare. This works a treat because my install instantly has a valid cert and all is right with the world…until, that is, I tried to connect Servicenow(SNOW) to Ascender’s API via Oauth. I kept getting an “HTTP Error 401 – Unauthorized” message when trying to grab an Oauth token via the Rest Messages.
I have a couple of blog posts on configuring SNOW integration with AAP if you are interested: Order VMs via SNOW, read SNOW CMDB, write SNOW CMDB.
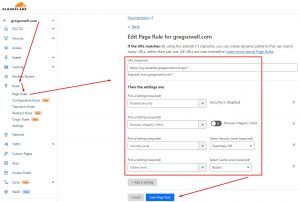
The fix is to make some adjustments in Cloudflare via Page Rules.
Once in Cloudflare, navigate to the domain in question, then click on the rules menu(from here it defaults to “Page Rules”, which is what we want).
In here create a new rule and fill it out as follows:
URL: https://ciq-ascender.gregsowell.com/api/*
Settings:
– Disable Security
– Browser Integrity Check: Off
– Security Level: Essentially Off
– Cache Level: Bypass
Good luck and happy Oauthing…LOL


Please show them some love on their socials here: https://engineerguy.com/, https://www.youtube.com/@engineerguyvideo/videos, https://twitter.com/engineerguytwit.

Please show them some love on their socials here: https://engineerguy.com/, https://www.youtube.com/@engineerguyvideo/videos, https://twitter.com/engineerguytwit.

Please show them some love on their socials here: https://www.robs10kfriends.com/, https://www.instagram.com/robs10kfriends/, http://roblawless.com/.

Please show them some love on their socials here: https://www.instagram.com/chuckhistory/?hl=en, https://www.facebook.com/thepeoplewalker/, https://www.tiktok.com/@chuckmccarthy?lang=en, https://www.chuckmccarthy.com/.
Occasionally I’ll be in an unfamiliar place and I want to plug into a switch and see what VLANs a trunk port will give me(I can also use this on wireless occasionally).
There are many ways to do this, but I figured this is a fairly simple one that doesn’t tax small devices too much.
Mikrotik Config
First thing I did was add a VLAN interface(which is virtual) to the physical interface my resource lives on. In my case it was just WLAN1
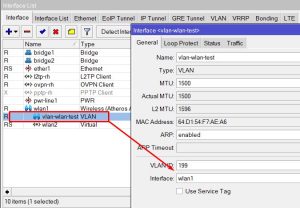
I then created a DHCP client interface.
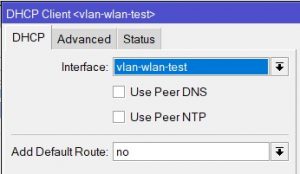
Now that I have that configured I wrote a simple script that will do all the work for me:
1 2 3 4 5 6 7 8 9 10 11 | :local i 2
:local x 200
:log info snooping-start
/ip dhcp-client enable [/ip dhcp-client find interface=vlan-wlan-test]
while ($i < $x) do={
/interface vlan set vlan-wlan-test vlan-id=$i
:log info "snooping $i"
:set $i ($i + 1)
:delay 5000ms
}
/ip dhcp-client disable [/ip dhcp-client find interface=vlan-wlan-test] |
Local i is what VLAN ID to start at.
Local x is the high number VLAN ID to stop at.
The idea is this script will enable the DHCP client, set the VLAN interface ID to the low number, sit there for 5 seconds, move to the next VLAN ID, and when it’s done it will disable the DHCP client.
The DHCP client will add an entry to the log if it is able to pull an IP.
So I can fire off the script, come back later and the log will tell me the VLAN ID along with the IP subnet it found there.
Conclusion
So this isn’t the most elegant way to perform the action, but it is pretty simple. It is predicated on the idea that DHCP must be there, so it could be modified to possibly do some snooping on each to find traffic.
Let me know what you would do differently, how would you modify it?
Thanks and happy VLAN finding.

