Cyberark Vault Integration With Ansible Tower
Cyberark has some impressive security tools, and in today’s example I’m using their Vault product. We are connecting in through their AIM(Application Identity Manager) system. Like other secrets engines, AIM allows me to pull secure credentials from it at run time. Also, I’d like to give a big shoutout to the team at CyberArk for providing us with this excellent demo environment!
**CyberArk PAM (depending on your software package) may require the below additional license to allow API access**
Product Code
APP-ISV-SUBS
Product Name
Secret management for commercial software (part of C3 integrations)
Description
Secret management for commercial software (part of C3 integrations). Price per single integration unit. Minimum purchase
of 5 integration units
Demo Video
CyberArk
First I create an application…honestly I was lazy and just used testappid.
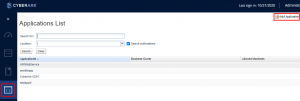
Next you add authentication certificates to use with the app.
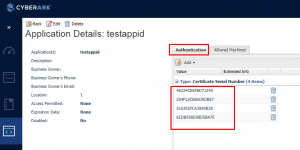
After this I browse to policies and hit access control. From here I add any safes that I need access to.
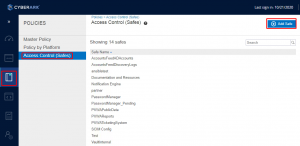
I then select the safe and edit the members list.
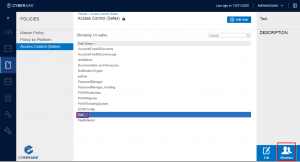
Add the app that needs access. I just wanted it to retrieve passwords, and not have any other access so, it only has retrieve.
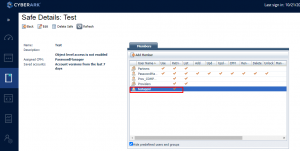
After this I pop into the vault.
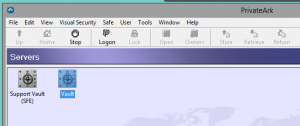
I open the safe in question. Here it’s “Test”.
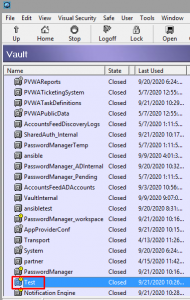
I then create a password object. In my case it’s “ansible” and the password is redhat. **After this hit the Logoff button**
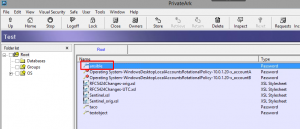
Tower Configuration
Tower has a custom credential lookup plugin to utilize CA AIM, which I’ll use as a lookup for other credentials.
First I add a new credential of type “CyberArk AIM Central Credential Provider Lookup”
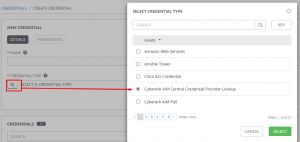
Next I put in my CA AIM URL, application id(in this case testappid), the client key, and the client cert.
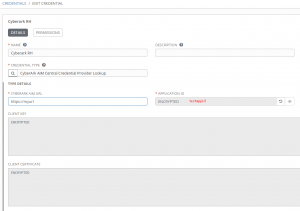
Now I create another standard credential of any type(in this instance I use a standard machine credential. For password I click the magnifying glass and it displays the Cyberark AIM credential I just created.
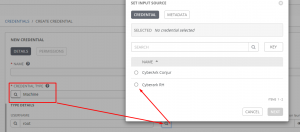
I now put in the object query based on the safe of Test and object of ansible.
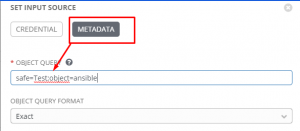
1 | safe=Test;object=ansible |
Github Scripts
Here is a demo script using a custom credential to display the ansible password:
As you can see, all of the magic is done in the lookup plugin, so nothing special to show here; that’s what’s so cool about the lookup(it’s so simple and clean).
Here’s another version updating the backup user on some Cisco switches:
Conclusion
It was a bear to figure all of this out, but once you have your head wrapped around it, it’s really quite simple. I really like how clean it all is.
If you have any questions or comments, please let me know.
Thanks and happy CyberArking 😉


How do you locate the client key and client certificates for usage within Ansible tower credentials?
I have an ansible tower cluster with 3 nodes and wish to integrate with Cyberark AIM, but cyberark team does not have much info pertaining to these client certs and client key for this? Can you elaborate or point me to right direction as to how we can avail these easily?
@Gagandeep The environment I was given already had the certs up and running. I *believe* that you can create a certificate via any method you like. Since this is windows you could use puttygen for example. Once you have that, you should add it to the local certificate store on the Windows machine. I think that at this point you can now specify the certificate serial number in your application for authentication.