Mikrotik Specific DHCP Address On Specific Interface
I had a customer ask for a very odd configuration.
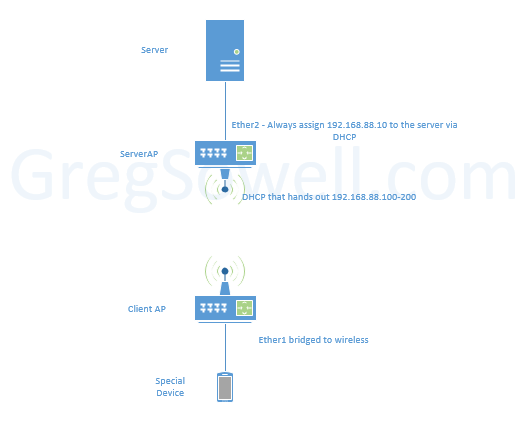
Off of the ServerAP, Ether 2 must always hand out 192.168.88.10. The routers need to be a generic config so they can use them no matter what MAC address the server has.
They also want the ClientAP to just bridge everything together so the remote special devices will pull DHCP from the server AP. Oh yeah…and they all have to be in the same “subnet” and accessible to each other. What to do, what to do…
Well, this is what I did:
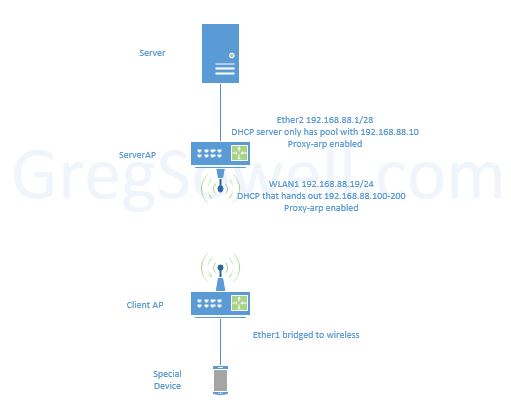
The ServerAP has proxy-arp enabled for both Ether2 and WLAN1.
I then set Ether2 to IP 192.168.88.1/28 and configured a DHCP server on it to only hand out 192.168.88.10. If you don’t add an interface with an IP, the DHCP won’t enable. I first thought about bridging Ether2 and WLAN1, but if you do this, you can only run a single DHCP server…which means we can’t set aside a special IP for the server. So by breaking the subnet up we can run multiple servers.
Ether2 is configured for 192.168.88.19/24 with a DHCP handing out 192.168.88.100-254.
The ClientAPs then run in station bridge to allow them to connect wirelessly and bridge their ether interfaces over. Now wired clients can pull DHCP from the ServerAP.
Here’s the configs:
ServerAP:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 | /interface ethernet
set [ find default-name=ether2 ] arp=proxy-arp
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
add authentication-types=wpa2-psk eap-methods="" management-protection=\
allowed mode=dynamic-keys name=profile1 supplicant-identity="" \
wpa2-pre-shared-key=popcorn
/interface wireless
set [ find default-name=wlan1 ] adaptive-noise-immunity=ap-and-client-mode \
arp=proxy-arp band=2ghz-b/g/n disabled=no mode=ap-bridge \
security-profile=profile1 ssid=p48923
/ip pool
add name=dhcp_pool1 ranges=192.168.88.10
add name=dhcp_pool2 ranges=192.168.88.100-192.168.88.254
/ip dhcp-server
add address-pool=dhcp_pool1 disabled=no interface=ether2 lease-time=30s name=\
dhcp1
add address-pool=dhcp_pool2 disabled=no interface=wlan1 lease-time=10m30s \
name=dhcp2
/ip address
add address=192.168.88.1/28 interface=ether2 network=192.168.88.0
add address=192.168.88.19/24 interface=wlan1 network=192.168.88.0
/ip dhcp-client
add default-route-distance=0 dhcp-options=hostname,clientid disabled=no \
interface=ether1
/ip dhcp-server network
add address=192.168.88.0/28 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.88.1
add address=192.168.88.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.88.19
/ip firewall nat
add action=masquerade chain=srcnat out-interface=ether1
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www address=192.168.88.0/24
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/system identity
set name=ServerAP |
ClientAP:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | /interface bridge
add name=bridge1
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
add authentication-types=wpa2-psk eap-methods="" management-protection=\
allowed mode=dynamic-keys name=profile1 supplicant-identity="" \
wpa2-pre-shared-key=popcorn
/interface wireless
set [ find default-name=wlan1 ] adaptive-noise-immunity=ap-and-client-mode \
band=2ghz-b/g/n disabled=no mode=station-bridge security-profile=profile1 \
ssid=p48923
/interface bridge port
add bridge=bridge1 interface=ether1
add bridge=bridge1 interface=ether2
add bridge=bridge1 interface=wlan1
/ip dhcp-client
add default-route-distance=0 dhcp-options=hostname,clientid interface=bridge1
/system identity
set name=ClientAP |
As odd as this config seems, it worked a treat. The real secret is that proxy-arp allows the devices on different subnets to communicate even though it seems as though they shouldn’t be able to.
This is a weird one for sure. How would you guys have approached this? What would you have done different?

