Protect Your Network From Mikrotik Exploits
Attacks on older versions of Mikrotik have stepped up recently. You can easily protect your network from such attacks in a couple of simple steps.
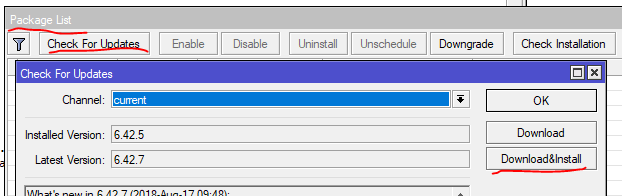
1. Update your Mikrotik to a new version that isn’t affected
1 | system package upgrade |
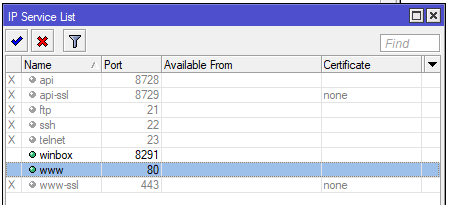
2. Disable any unneeded Mikrotik services
1 2 | ip services dis 0,1,2,3,4,7 |
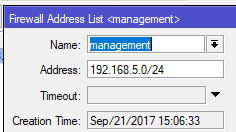
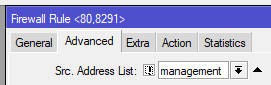
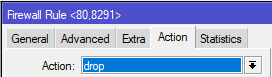
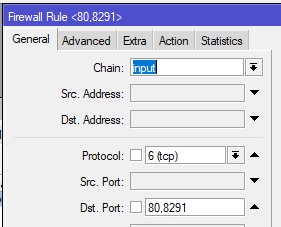
3. Add firewall rules to protect those services – be sure to drag it to the top of the list
1 2 3 4 5 6 7 | /ip firewall address-list # create an address-list where management traffic will be sourced from add address=192.168.5.0/24 list=management /ip firewall filter # create a firewall drop rule that will block access to the allowed ip services if it's not from the management subnet add action=drop chain=input dst-port=80,8291 protocol=tcp src-address-list=!management |
If you would like to protect Mikrotiks inside of your network, you should apply similar rules to the forward chain of your border routers.
This obviously isn’t a complete security policy, or all of the firewall rules you should have in place, but it will at a minimum stop attacks.
If you have been comprimised, you really should update, then verify no new users, firewall rules, socks, or web proxies are in place.
You then need to change all of your user/password combos as part of the exploits is extraction of the user database!
You should update ASAP. A best strategy would be to reset the configuration, update, and rebuild.