Mikrotik Firewall Raw Feature Test
While talking about doing a podcast on DoS protection it was brought to my attention that Mikrotik added a new firewall feature (Raw). Raw is a mechanism to less granularly, but more efficiently drop traffic in the router.
Raw is configured similarly to a standard firewall rule, but it will drop traffic BEFORE it has an opportunity to hit the connection tracking table. In the packetflow diagram you will see it juuuust before the connection tracking. It has a chain of prerouting and output.
My testing consists of a nice low powered RB750 running 6.36rc21(this is the first version with the Raw feature). I wanted a nice low powered single proc device so I wouldn’t have to push it too hard to see results.
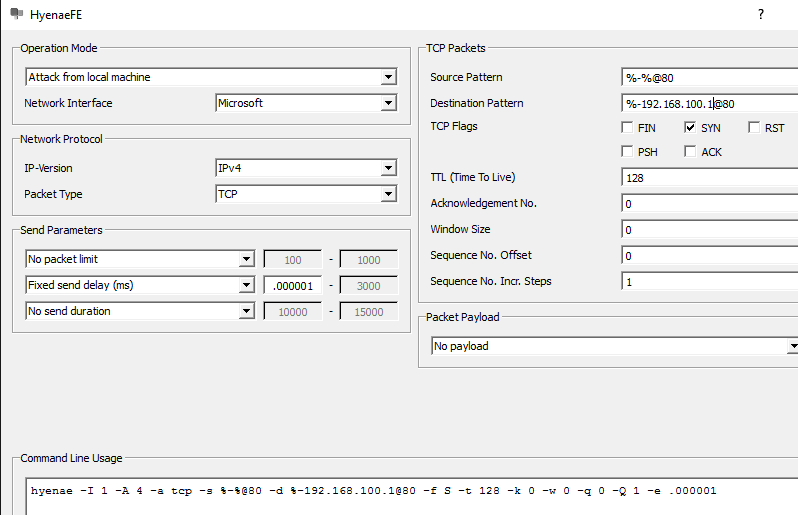
My traffic generator is Hyenae running a TCP SYN attack. This was my first time to use Hyenae, and I was delighted with the results. It runs pretty cleanly and can generate a whole host of attacks…I actually had to set a fixed send delay because it was tipping the 750 over hehehe. The one thing I didn’t understand was the destination/source pattern settings.
It defaults to %-%@80.
The first % sign is a wildcard that says “randomly generate a MAC address”.
The second % sign says randomly generate an IP address, and the @80 means use port 80.
For example you could set a mac address and IP like so: 00:00:00:00:00:01-1.1.1.1@80
You can see in my example below I attacked my router directly by specifying its IP and didn’t worry about the MAC.
The Raw option can be found in “/ip firewall raw”. It’s also already in winbox at the same location:
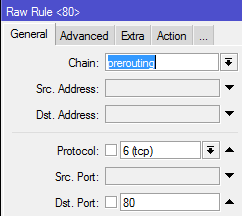
For my testing I DoS’d the router with a SYN attack to port 80. I created a Raw rule and a standard Filter rule.
My Raw rule is:
1 2 3 | /ip firewall raw
add action=drop chain=prerouting disabled=yes dst-port=80 log=no log-prefix="" \
protocol=tcp |
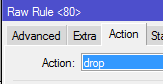
Then I created my Filter rule on the input chain…input because the traffic is destined TO the router.
1 2 | /ip firewall filter add action=drop chain=input disabled=no dst-port=80 log=no log-prefix="" protocol=tcp |
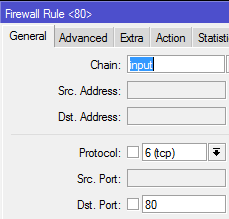
When you start looking at the Raw command you will immediately notice there are a lot of knobs that are missing. I’m no rocket surgeon, but I assume it is due to doing the filtering so early in the system. Here’s a side by side of just the initial screen(Filter on the left, Raw on the right):
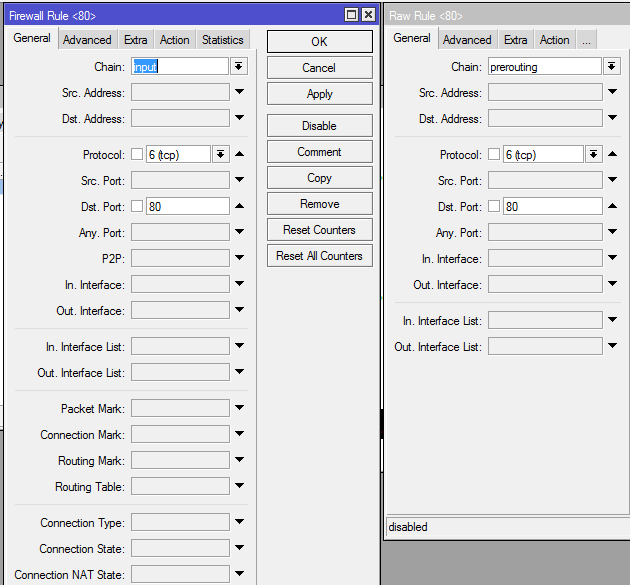
Now for the quick test. I start with both rules enabled. Since the Raw rule catches first, the Filter rule isn’t hit. This is evidenced by the counter. With the Raw rule enabled we are averaging about 5% CPU:
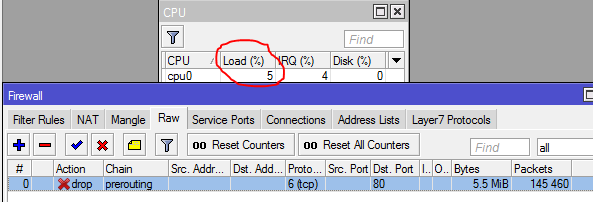
I then disable the Raw rule and let the Filter rule take over:
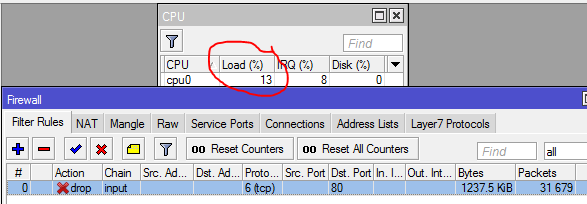
As you can see the filter rule is averaging about 13% on the CPU.
Conclusion
The Raw rule in my basic testing shows around an 8% savings in CPU over a standard Filter rule. I’ve also heard reports of 6 fold savings in the CCR platform! As described to me, this can be an invaluable tool in DoS/DDoS attacks. It could be the difference between your router tipping over from attack or hanging on and keeping you online.
This Raw system can also still be pretty flexible since it can utilize address-lists identified by the Mangle or Filter systems. Once this gets ported to a stable version I plan to make some adjustments to my basic firewall scripts to take advantage of the Raw system. I’m not sure of any other implications(does this affect FastPath or queuing…I don’t know?!?!)
Let me know what you guys think…how do you see yourself utilizing this in your networks?


New feature “Raw” looks pretty impressive. Thanks for sharing your experience. I`ll test with L2 looped network, which has huge impact on RouterOS. As u mentioned fastpath, queue are other important parts should consider and test.
Good luck.
@Otgooneo, let me know how it goes!